Search Results for author: Xueluan Gong
Found 3 papers, 1 papers with code
Backdoor Attack with Sparse and Invisible Trigger
1 code implementation • 11 May 2023 • Yinghua Gao, Yiming Li, Xueluan Gong, Zhifeng Li, Shu-Tao Xia, Qian Wang
More importantly, it is not feasible to simply combine existing methods to design an effective sparse and invisible backdoor attack.
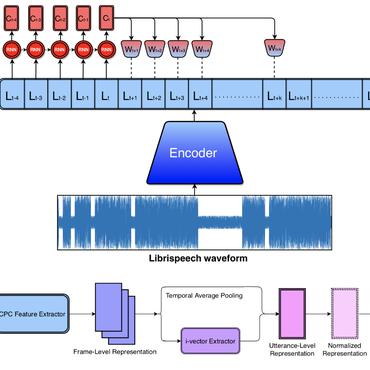
Catch You and I Can: Revealing Source Voiceprint Against Voice Conversion
no code implementations • 24 Feb 2023 • Jiangyi Deng, Yanjiao Chen, Yinan Zhong, Qianhao Miao, Xueluan Gong, Wenyuan Xu
Voice conversion (VC) techniques can be abused by malicious parties to transform their audios to sound like a target speaker, making it hard for a human being or a speaker verification/identification system to trace the source speaker.
MARNET: Backdoor Attacks against Value-Decomposition Multi-Agent Reinforcement Learning
no code implementations • 29 Sep 2021 • Yanjiao Chen, Zhicong Zheng, Xueluan Gong
Recent works have revealed that backdoor attacks against Deep Reinforcement Learning (DRL) could lead to abnormal action selection of the agent, which may result in failure or even catastrophe in crucial decision processes.