Search Results for author: Gianluca Stringhini
Found 28 papers, 4 papers with code
Cerberus: Exploring Federated Prediction of Security Events
no code implementations • 7 Sep 2022 • Mohammad Naseri, Yufei Han, Enrico Mariconti, Yun Shen, Gianluca Stringhini, Emiliano De Cristofaro
Modern defenses against cyberattacks increasingly rely on proactive approaches, e. g., to predict the adversary's next actions based on past events.
Why So Toxic? Measuring and Triggering Toxic Behavior in Open-Domain Chatbots
no code implementations • 7 Sep 2022 • Wai Man Si, Michael Backes, Jeremy Blackburn, Emiliano De Cristofaro, Gianluca Stringhini, Savvas Zannettou, Yang Zhang
We show that publicly available chatbots are prone to providing toxic responses when fed toxic queries.
Finding MNEMON: Reviving Memories of Node Embeddings
no code implementations • 14 Apr 2022 • Yun Shen, Yufei Han, Zhikun Zhang, Min Chen, Ting Yu, Michael Backes, Yang Zhang, Gianluca Stringhini
Previous security research efforts orbiting around graphs have been exclusively focusing on either (de-)anonymizing the graphs or understanding the security and privacy issues of graph neural networks.
Feels Bad Man: Dissecting Automated Hateful Meme Detection Through the Lens of Facebook's Challenge
no code implementations • 17 Feb 2022 • Catherine Jennifer, Fatemeh Tahmasbi, Jeremy Blackburn, Gianluca Stringhini, Savvas Zannettou, Emiliano De Cristofaro
Internet memes have become a dominant method of communication; at the same time, however, they are also increasingly being used to advocate extremism and foster derogatory beliefs.
Slapping Cats, Bopping Heads, and Oreo Shakes: Understanding Indicators of Virality in TikTok Short Videos
no code implementations • 3 Nov 2021 • Chen Ling, Jeremy Blackburn, Emiliano De Cristofaro, Gianluca Stringhini
We do so vis-\`a-vis three research hypotheses; namely, that: 1) the video content, 2) TikTok's recommendation algorithm, and 3) the popularity of the video creator contribute to virality.
ANDR USPEX : Leveraging Graph Representation Learning to Predict Harmful App Installations on Mobile Devices
no code implementations • 9 Mar 2021 • Yun Shen, Gianluca Stringhini
Unlike commodity anti-malware solutions on desktop systems, their Android counterparts run as sandboxed applications without root privileges and are limited by Android's permission system.
 Graph Representation Learning
Cryptography and Security
Graph Representation Learning
Cryptography and Security
Understanding Worldwide Private Information Collection on Android
no code implementations • 25 Feb 2021 • Yun Shen, Pierre-Antoine Vervier, Gianluca Stringhini
Mobile phones enable the collection of a wealth of private information, from unique identifiers (e. g., email addresses), to a user's location, to their text messages.
 Mobile Security
Cryptography and Security
Mobile Security
Cryptography and Security
The Gospel According to Q: Understanding the QAnon Conspiracy from the Perspective of Canonical Information
no code implementations • 21 Jan 2021 • Max Aliapoulios, Antonis Papasavva, Cameron Ballard, Emiliano De Cristofaro, Gianluca Stringhini, Savvas Zannettou, Jeremy Blackburn
By interpreting cryptic "drops" of information from an anonymous insider calling themself Q, adherents of the conspiracy theory believe that Donald Trump is leading them in an active fight against this cabal.
Computers and Society Social and Information Networks
An Early Look at the Parler Online Social Network
no code implementations • 11 Jan 2021 • Max Aliapoulios, Emmi Bevensee, Jeremy Blackburn, Emiliano De Cristofaro, Gianluca Stringhini, Savvas Zannettou
Parler is as an "alternative" social network promoting itself as a service that allows to "speak freely and express yourself openly, without fear of being deplatformed for your views."
Social and Information Networks Computers and Society Physics and Society
"Go eat a bat, Chang!": On the Emergence of Sinophobic Behavior on Web Communities in the Face of COVID-19
no code implementations • 8 Apr 2020 • Fatemeh Tahmasbi, Leonard Schild, Chen Ling, Jeremy Blackburn, Gianluca Stringhini, Yang Zhang, Savvas Zannettou
Finally, we find interesting differences in the context in which words related to Chinese people are used on the Web before and after the COVID-19 outbreak: on Twitter we observe a shift towards blaming China for the situation, while on /pol/ we find a shift towards using more (and new) Sinophobic slurs.
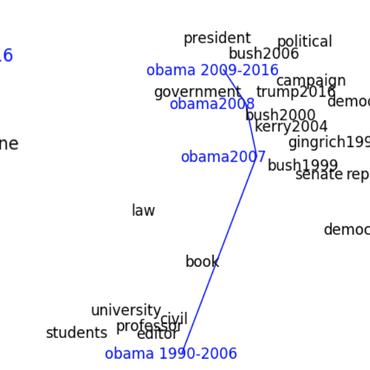 Word Embeddings
Social and Information Networks
Computers and Society
Word Embeddings
Social and Information Networks
Computers and Society
"How over is it?" Understanding the Incel Community on YouTube
no code implementations • 22 Jan 2020 • Kostantinos Papadamou, Savvas Zannettou, Jeremy Blackburn, Emiliano De Cristofaro, Gianluca Stringhini, Michael Sirivianos
YouTube is by far the largest host of user-generated video content worldwide.
Computers and Society
The Evolution of the Manosphere Across the Web
no code implementations • 21 Jan 2020 • Manoel Horta Ribeiro, Jeremy Blackburn, Barry Bradlyn, Emiliano De Cristofaro, Gianluca Stringhini, Summer Long, Stephanie Greenberg, Savvas Zannettou
In this paper, we present a large-scale characterization of the Manosphere, a conglomerate of Web-based misogynist movements roughly focused on "men's issues," which has seen significant growth over the past years.
Computers and Society
Detecting Cyberbullying and Cyberaggression in Social Media
no code implementations • 20 Jul 2019 • Despoina Chatzakou, Ilias Leontiadis, Jeremy Blackburn, Emiliano De Cristofaro, Gianluca Stringhini, Athena Vakali, Nicolas Kourtellis
We also explore specific manifestations of abusive behavior, i. e., cyberbullying and cyberaggression, in one of the hate-related communities (Gamergate).
ATTACK2VEC: Leveraging Temporal Word Embeddings to Understand the Evolution of Cyberattacks
no code implementations • 29 May 2019 • Yun Shen, Gianluca Stringhini
Despite the fact that cyberattacks are constantly growing in complexity, the research community still lacks effective tools to easily monitor and understand them.
Tiresias: Predicting Security Events Through Deep Learning
no code implementations • 24 May 2019 • Yun Shen, Enrico Mariconti, Pierre-Antoine Vervier, Gianluca Stringhini
With the increased complexity of modern computer attacks, there is a need for defenders not only to detect malicious activity as it happens, but also to predict the specific steps that will be taken by an adversary when performing an attack.
On the Origins of Memes by Means of Fringe Web Communities
2 code implementations • 31 May 2018 • Savvas Zannettou, Tristan Caulfield, Jeremy Blackburn, Emiliano De Cristofaro, Michael Sirivianos, Gianluca Stringhini, Guillermo Suarez-Tangil
In this paper, we detect and measure the propagation of memes across multiple Web communities, using a processing pipeline based on perceptual hashing and clustering techniques, and a dataset of 160M images from 2. 6B posts gathered from Twitter, Reddit, 4chan's Politically Incorrect board (/pol/), and Gab, over the course of 13 months.
Social and Information Networks Computers and Society
You are your Metadata: Identification and Obfuscation of Social Media Users using Metadata Information
no code implementations • 27 Mar 2018 • Beatrice Perez, Mirco Musolesi, Gianluca Stringhini
Metadata are associated to most of the information we produce in our daily interactions and communication in the digital world.
A Family of Droids -- Android Malware Detection via Behavioral Modeling: Static vs Dynamic Analysis
no code implementations • 9 Mar 2018 • Lucky Onwuzurike, Mario Almeida, Enrico Mariconti, Jeremy Blackburn, Gianluca Stringhini, Emiliano De Cristofaro
Aiming to counter them, detection techniques based on either static or dynamic analysis that model Android malware, have been proposed.
Cryptography and Security
Large Scale Crowdsourcing and Characterization of Twitter Abusive Behavior
7 code implementations • 1 Feb 2018 • Antigoni-Maria Founta, Constantinos Djouvas, Despoina Chatzakou, Ilias Leontiadis, Jeremy Blackburn, Gianluca Stringhini, Athena Vakali, Michael Sirivianos, Nicolas Kourtellis
In recent years, offensive, abusive and hateful language, sexism, racism and other types of aggressive and cyberbullying behavior have been manifesting with increased frequency, and in many online social media platforms.
Social and Information Networks 68T06 K.4.2
Understanding Web Archiving Services and Their (Mis)Use on Social Media
no code implementations • 31 Jan 2018 • Savvas Zannettou, Jeremy Blackburn, Emiliano De Cristofaro, Michael Sirivianos, Gianluca Stringhini
Web archiving services play an increasingly important role in today's information ecosystem, by ensuring the continuing availability of information, or by deliberately caching content that might get deleted or removed.
Computers and Society Digital Libraries Social and Information Networks
Eight Years of Rider Measurement in the Android Malware Ecosystem: Evolution and Lessons Learned
1 code implementation • 24 Jan 2018 • Guillermo Suarez-Tangil, Gianluca Stringhini
In this paper, we conduct the largest measurement of Android malware behavior to date, analyzing over 1. 2 million malware samples that belong to 1. 2K families over a period of eight years (from 2010 to 2017).
Cryptography and Security
MaMaDroid: Detecting Android Malware by Building Markov Chains of Behavioral Models (Extended Version)
no code implementations • 20 Nov 2017 • Lucky Onwuzurike, Enrico Mariconti, Panagiotis Andriotis, Emiliano De Cristofaro, Gordon Ross, Gianluca Stringhini
Aiming to assess whether MaMaDroid's effectiveness mainly stems from the API abstraction or from the sequencing modeling, we also evaluate a variant of it that uses frequency (instead of sequences), of abstracted API calls.
Class-based Prediction Errors to Detect Hate Speech with Out-of-vocabulary Words
no code implementations • WS 2017 • Joan Serr{\`a}, Ilias Leontiadis, Dimitris Spathis, Gianluca Stringhini, Jeremy Blackburn, Athena Vakali
Common approaches to text categorization essentially rely either on n-gram counts or on word embeddings.
Email Babel: Does Language Affect Criminal Activity in Compromised Webmail Accounts?
no code implementations • 25 Apr 2017 • Emeric Bernard-Jones, Jeremiah Onaolapo, Gianluca Stringhini
In summary, we show that language plays a significant role in the ability of cybercriminals to access sensitive information hidden in compromised webmail accounts.
Measuring #GamerGate: A Tale of Hate, Sexism, and Bullying
no code implementations • 24 Feb 2017 • Despoina Chatzakou, Nicolas Kourtellis, Jeremy Blackburn, Emiliano De Cristofaro, Gianluca Stringhini, Athena Vakali
Over the past few years, online aggression and abusive behaviors have occurred in many different forms and on a variety of platforms.
Mean Birds: Detecting Aggression and Bullying on Twitter
1 code implementation • 22 Feb 2017 • Despoina Chatzakou, Nicolas Kourtellis, Jeremy Blackburn, Emiliano De Cristofaro, Gianluca Stringhini, Athena Vakali
In recent years, bullying and aggression against users on social media have grown significantly, causing serious consequences to victims of all demographics.
Computers and Society Social and Information Networks
MaMaDroid: Detecting Android Malware by Building Markov Chains of Behavioral Models
no code implementations • 13 Dec 2016 • Enrico Mariconti, Lucky Onwuzurike, Panagiotis Andriotis, Emiliano De Cristofaro, Gordon Ross, Gianluca Stringhini
Finally, we compare against DroidAPIMiner, a state-of-the-art system that relies on the frequency of API calls performed by apps, showing that MaMaDroid significantly outperforms it.
Cryptography and Security
Kissing Cuisines: Exploring Worldwide Culinary Habits on the Web
no code implementations • 26 Oct 2016 • Sina Sajadmanesh, Sina Jafarzadeh, Seyed Ali Osia, Hamid R. Rabiee, Hamed Haddadi, Yelena Mejova, Mirco Musolesi, Emiliano De Cristofaro, Gianluca Stringhini
In this paper, we present a large-scale study of recipes published on the web and their content, aiming to understand cuisines and culinary habits around the world.

