BRON -- Linking Attack Tactics, Techniques, and Patterns with Defensive Weaknesses, Vulnerabilities and Affected Platform Configurations
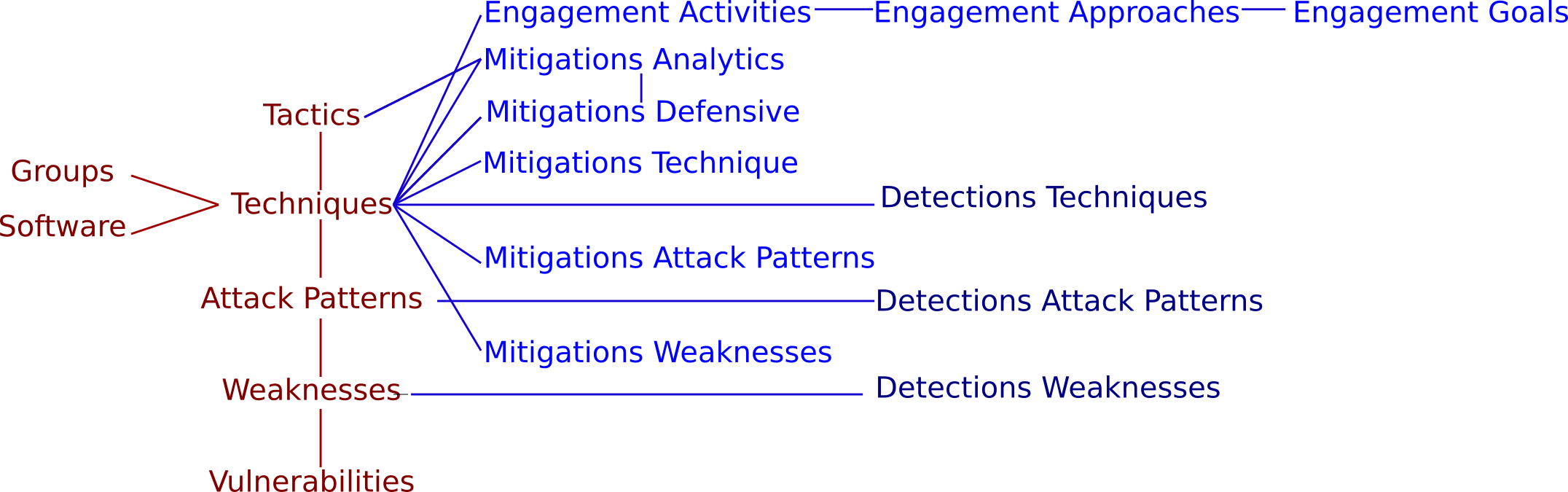
Many public sources of cyber threat and vulnerability information exist to serve the defense of cyber systems. This paper proposes BRON which is a composite of MITRE's ATT&CK MATRIX, NIST's Common Weakness Enumerations (CWE), Common Vulnerabilities and Exposures (CVE), and Common Attack Pattern Enumeration and Classification, CAPEC. BRON preserves all entries and relations while enabling bi-directional, relational path tracing. It exploits attack patterns to trace between the objectives and means of attacks to the vulnerabilities and affected software and hardware configurations they target. We inventory and analyze BRON's sources to gauge any gap between information on attacks and information on attack targets. We also analyze BRON for information that is a by-product of its mission.
PDF Abstract